Overview
Project Telescope is an open-source initiative which intends to allow organizations that are hosting applications on OpenShift Container Platform to enhance their security governance, risk, and compliance capabilities through a novel implementation of automation, visualization, and metadata consolidation, in a customizable and extensible manner.
What’s the problem space?
Project Telescope was born out of a recurring challenge identified through engagements with various organizations across multiple industry verticals: a growing number of organizations are recognizing the necessity of digitally transforming their business by modernizing their IT landscape and development culture. Simultaneously, these organizations are becoming more aware of the ever-increasing need to secure these digital offerings as cyber attacks are rising in frequency and impact at a terrifying rate.
Increasingly, organizations are finding these two needs - transformative digital adoption and a growing requirement for cyber security - to be diametrically opposed. This is due to a combination of an inability to keep pace with the scale and speed of modern development and a reliance on legacy governance, risk, and compliance processes. These policies include architectural design boards, review committees, and lengthy audits which can stifle innovation. In some organization’s, this is resulting in a development culture whereby products are only achieving security accreditation 50% of the time, and taking an average of nine months to do so. This is simply untenable.
What is needed?
What’s needed is a capability which would do the following:
- In a fully automated manner, allow organizations to define their own mandate for technical security requirements and compliance. Not only compliance to industry frameworks or regulations, but a set of requirements to adhere to minimum viable standards as defined by the organization themselves.
- Ensure that these requirements are being met by all DevSecOps teams.
- Display the status of compliance to the security team.
- Correlate discovered vulnerabilities to business risk, all in real time.
How does Project Telescope solve this?
In order to provide the maximum level of coverage, Project Telescope works like this:
- Project Telescope will be deployed in a users existing OpenShift environment
- Users will input information into a weighted Business Impact Assessment (BIA) questionnaire
- This information can be changed and updated at any time.
- The questionnaire will capture information regarding the user’s risk appetite. An example could be A mapping of both the financial and operational amounts of loss to risk criticality, business critical application status, etc.
- The results will inform Project Telescope’s Risk Correlation Engine during the risk assessment phase of use.
- The results will be stored in a back-end database to allow for historic data comparisons and visualizations.
- API integrations will be made from the Project Telescope deployment to the various existing security tools and technologies in the user’s environment which correlate to various security domain mandates.
- Out of the box, Project Telescope will provide recommendations across a variety of pre-determined security domains.
- However, a major value of Project Telescope is that it enables users to add, remove, and alter the various mandate checks, so as to be truly agnostic and extensible to the user’s needs.
- A series of automated queries will be leveraged against the various security tools in order to gauge the state of compliance to the user’s mandate.
- Project Telescope will also provide pseudo-code architectural patterns enabling users to write their own integrations and queries for mandates beyond the initial options.
- The results of these queries will return to and be stored in the back-end database. The Project Telescope dashboard will simultaneously pull the results for display to the users.
- The results of various security tool’s vulnerability scans and assessments will also be pulled to the back-end database. These include, but are not limited to:
- Publicly available information from the NVD CVE database
- The MITRE ATT&CK framework
- The BIA questionnaire will funnel into the Risk Correlation Engine which will generate a risk score, with financial impact assessment.
- The results are output to the Project Telescope database and dashboard
Architecture
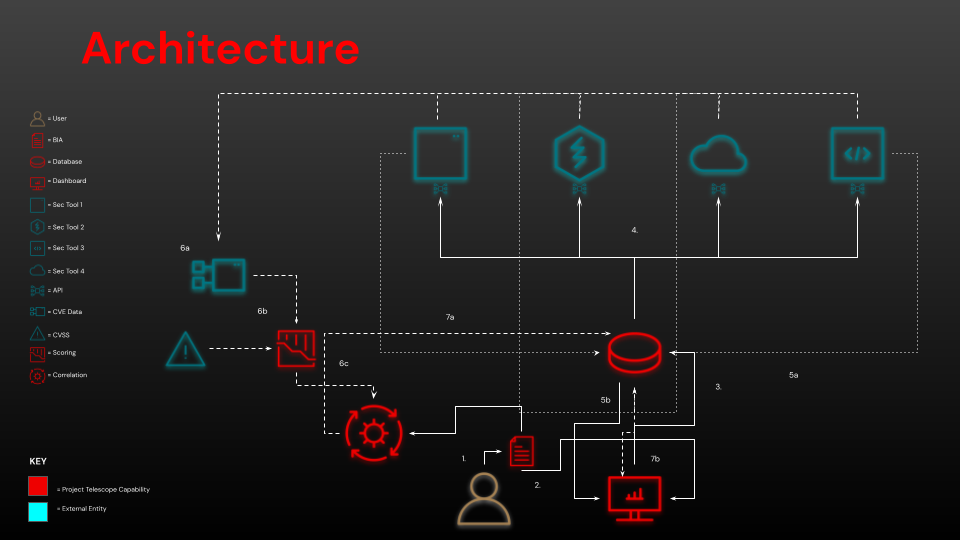
This sounds complicated - how do I use it?
At this point, it may be valuable to explain why we’ve chosen the name Project Telescope. Through a single dashboard, there are varying levels of focus, or “lenses” through which a user can view the capability depending on their persona within the organization:
- The first lens is the Operator Lens. It enables DevOps teams to see, in real time, the binary state of their product’s compliance to various technical security mandates. Furthermore, it will show the reason for technical compliance failure, allowing DevOps teams to rectify failures themselves, without needing to wait for outside assistance.
- The second lens is the Owner Lens, which provides value to a Product Owner. While the user will still see the state of compliance to mandate, they will also see the results of the Risk Correlation Engine assessment, providing a mapping of existing vulnerabilities in the product to financial risk, as defined by the user.
- The final lens is the Executive Lens; this services Platform or Executive leadership by aggregating the Owner’s Lens results for all Project Telescope installations across an organizational platform. This will allow leadership to accurately demonstrate the state of risk and compliance of their platform over time.
Summary
Project Telescope is less of a cyber security tool, and more a "manual process demolisher". The aims of this capability are to provide real time, fully automated cyber security governance, risk, and compliance capabilities across a set of user-defined technical mandates, and enable users to accurately understand their risk landscape and compliance failures.
The ultimate goal is to enable end users to become demonstrably more secure, faster